¶ System Requirements
Below are the system requirements in order for CloudPanel to operate correctly:
- Windows Server 2019 and 2022
- Domain controller must be configured for port 636 (LDAPS) and if using a self-signed certificate (without a public or private certificate authority), you may need to install the SSL in the Trusted Root folder on the CloudPanel server.
- IIS installed with ASP.NET 4.7.2 or later
- Powershell 5.0 or later
- Microsoft .NET Framework 4.7.2 or later
- Microsoft SQL Server 2017, 2019, and 2022
- Microsoft Exchange 2016 or 2019
- Microsoft Exchange must be installed on its own server. You cannot install Exchange on a domain controller
- Optional: Active Directory in List Object Mode (https://social.technet.microsoft.com/wiki/contents/articles/29558.active-directory-controlling-object-visibility-list-object-mode.aspx#Enable_List_Object_Mode)
¶ Microsoft SQL
During the installation of CloudPanel, it will create the database using the account you are logged in with. You need to make sure the account you are logged in with has access to SQL and the service account you end up using has access:
Roles: public, dbcreator
If you have an existing database, make sure it has DBO permissions to that database.
¶ Prepare Active Directory
CloudPanel places all reseller and company objects inside a “Hosting” organizational unit that you create. This organizational unit can be located wherever you would like and be named whatever you want.
- Create a new organizational unit (or use existing one) in any location that you want to store all reseller and company objects which include users, contacts, groups, and more. This will be referred to as the “hosting organizational unit”.
- Create a new organizational unit called Applications inside your hosting organizational unit.
- Inside the Hosting organizational unit create two security groups named exactly: AllTSUsers@Hosting and GPOAccess@Hosting
It is recommended to enable the Active Directory recycle bin in your environment. This will help you restore Active Directory objects without having to restore them from backups
¶ LDAPS Requirement
CloudPanel uses port 636 only which is LDAPS. If you do not have a certificate authority in your environment, you can configure a self-signed SSL on the domain controller(s) by following these instructions:
- Open Powershell as administrator on the domain controller
- Run the following command:
- New-SelfSignedCertificate -DnsName “<fully qualified domain name>”,"<netbios name>" -CertStoreLocation cert:\LocalMachine\My
- Replace “<fully qualified domain name>” with the FQDN of the server you are on. Example: DC01.domain.local
- Replace “<netbios name>" with the server name you are on. Example: DC01
- Export this new SSL without the private key to a location on your network
- Import this new SSL in the Trusted Root Certification Authority folder of the Local Computer so it will be trusted. Do this on the CloudPanel server as well if you run into any issues with it connecting.
- New-SelfSignedCertificate -DnsName “<fully qualified domain name>”,"<netbios name>" -CertStoreLocation cert:\LocalMachine\My
¶ Active Directory Account
Adding the CloudPanel account to the Domain Admins group and Exchange Organization Management group will work and is the easy configuration, but this gives CloudPanel the most privileges in your network.
If you want to limit the scope that the service account has access to, please follow the instructions below. Right click on the “Hosting” organizational unit you created above and add the following permissions:
| OU | Applies To | Permissions Needed |
| Hosting | Descendant Contact objects | List contents, read all properties, write all properties, delete, send as |
| Hosting | Descendant Group objects | List contents, read all properties, write all properties, delete, modify permissions, send as, send to |
| Hosting | Descendant User objects | List contents, read all properties, write all properties, delete, delete subtree, modify permissions, create all child objects, change password, receive as, reset password, send as |
| Hosting | Descendant Organizational Unit objects | List contents, read all properties, delete, delete subtree, modify permissions, modify owner, create account objects, delete account objects, create contact objects, delete contact objects, create group objects, delete group objects, create user objects, delete user objects, create organizational unit objects, delete organizational unit objects, write all properties |
| Hosting | This object only | List contents, read all properties, read permissions, create organizational unit objects, delete organizational unit objects |
In Active Directory Users & Computes snap-in, enable advanced features and expand System, then right click on “Password Settings Container”:
| Folder Object | Applies To | Permissions Needed |
| Password Settings Container | This object only | List contents, read all properties, read permissions, Create msDS-PasswordSettings objects |
| Password Settings Container | Descendant msDS-PasswordSettings objects | List contents, read all properties, write all properties, delete, read permissions |
¶ CloudPanel Server Permissions (If using granular permissions)
Add the CloudPanel account you created to the local administrators group on your CloudPanel server. If you installed your CloudPanel instance on a domain controller or a Exchange server, then using granular permissions is going to be difficult and is not covered in this documentation.
¶ Microsoft Exchange Limited Permissions (If using granular permissions)
Instead of adding the CloudPanel account to the Exchange Organization Management group, you can also create a custom admin role which can limit writing to specific organizational units. The example below shows how to setup this configuration, but if you prefer to add the CloudPanel service account to the Domain Admins group, then this will not be neccessary.
Create a custom write scope in Exchange to limit the scope to the Hosting organizational unit and all child objects:
New-ManagementScope -Name "CloudPanel Write Scope" -RecipientRoot "dev.knowmoreit.io/Hosting" -RecipientRestrictionFilter "RecipientType -LIKE '*'"
Login to Exchange ECP, go to Permissions, select admin roles and add a new admin role:
| Name | CloudPanel Admin Role |
| Description | Custom role used to limit the scope of the CloudPanel service account that runs the CloudPanel application and Windows service |
| Write Scope | Choose: “CloudPanel Write Scope” that you created above |
| Roles |
Active Directory Permissions, Address Lists, Databases, Distribution Groups, Legal Hold, LegalHoldApplication, Mail Enabled Public Folders, Mail Recipient Creation, Mail Recipients, Message Tracking, POP3 and IMAP4 Protocols, Public Folders, Remote and Accepted Domains, Security Group Creation and Membership, User Options, Retention Management, Recipient Policies Additional roles that may be needed |
| Members | Add your CloudPanel service account |
¶ Prepare Microsoft Exchange
CloudPanel uses Address Book Policies to keep your customers information separate from each other. Address Book Policies were created in Exchange 2010 SP2 and is Microsoft’s new way of providing a multi-tenant environment for Exchange server. There are some things that they left out that could still expose information between tenants.
¶ Secure the Offline Address Book
The following two commands should be run once per Exchange installation to remove the MS-Exch-Download-OAB extended right from the root OAB container. This prevents all subsequently created OABs from inheriting this extended right.
Each of the following examples assumes the domain being used by the hoster is called fabrikam.com, you need to change the examples shown below to refer to your own deployment.
$BaseOABContainer="CN=Offline Address Lists,CN=Address Lists Container,CN=First Organization,CN=Microsoft Exchange,CN=Services,CN=Configuration,DC=Fabrikam,DC=com"
Get-ADPermission $BaseOABContainer -User "NT Authority\Authenticated Users" |WHERE extendedrights -match "ms-exch-download-oab" | Remove-ADPermission
¶ Hide the “Groups” section in OWA (Exchange 2010/2013)
Note: This is not needed for Exchange 2016 or later, however you will need to modify the Role Assignment in CloudPanel under the Advanced section on the Exchange tab in the CloudPanel settings.
By default users will be able to see other company’s distribution groups when they are logging into the web interface. To resolve this we either need create an alternate role or modify what features are in this role. To begin open the Exchange Management Shell and enter the follow commands (make sure you Exchange environment is fully patched):
New-RoleAssignmentPolicy "Alternate Assignment Policy"
New-ManagementRoleAssignment -Name "MyContactInformation-Alternate Assignment Policy" -policy "Alternate Assignment Policy" -role MyContactInformation
New-ManagementRole "MyBaseOptionsWithoutMessageTracking" -Parent MyBaseOptions
Remove-ManagementRoleEntry "MyBaseOptionsWithoutMessageTracking\Search-MessageTrackingReport"
New-ManagementRoleAssignment -Name "MyBaseOptionsWithoutMessageTracking-Alternate Assignment Policy" -policy "Alternate Assignment Policy" -role MyBaseOptionsWithoutMessageTracking
¶ Mailtips
Mailtips are included with Exchange but can expose information between customers. We can’t simply disable Mailtips because the users will see an error in Outlook saying something about mailtips are disabled. Most likely you will get called about this. To resolve it we simple tell Exchange not to trigger Mailtips unless they are emailing a mass amount of people (which you set this number higher than what you would allow a user to email):
Set-OrganizationConfig -MailTipsExternalRecipientsTipsEnabled $False -MailTipsLargeAudienceThreshold 1000 -MailTipsMailboxSourcedTipsEnabled $False -MailTipsGroupMetricsEnabled $False -MailTipsAllTipsEnabled $True
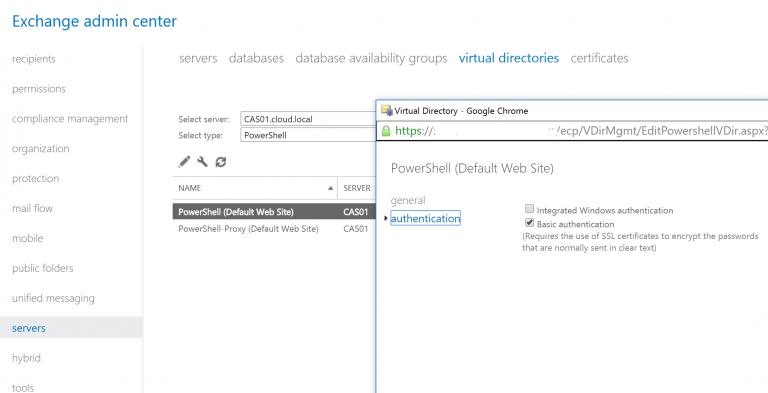
¶ Enable Basic Authentication on Powershell Virtual Directory
If you are planning on setting CloudPanel to use Basic Authentication (recommended) instead of Kerberos when calling powershell commands on Exchange then you must enable Basic Authentication on the powershell virtual directory. You only need to do this on the Exchange server you are configuring CloudPanel to communicate with.
Also make sure you are enabling basic authentication using ECP / EAC and not directly on IIS.
Sometimes new updates to Exchange can cause this setting to reset.